CHERI-based Prototype to Be Developed by Arm
Article By : Nitin Dahad
Britain is funding a new protection model to be applied to Arm ISA to enable next generation security.
A UK government program to tackle the inherent security flaws in most of today’s computing infrastructure is funding Arm to the tune of $46 million (UK £36 million) to develop a prototype board using CHERI, a DARPA supported RISC processor ISA update that uses capability-based tokens for fine-grained memory protection and scalable software compartmentalization.
The British government announced it is funding Arm to develop new technologies that are more resistant to cyber threats, as part of its wider ‘Digital Security by Design’ (DSbD) initiative. The latter is also backed by Google and Microsoft. Arm chief architect and Fellow Richard Grisenthwaite commented, “Our first step is to create prototype hardware, the Morello Board, as a real-world test platform for prototype architecture developed by Arm that uses the University of Cambridge’s CHERI protection model. It will enable industry and academic partners to assess the security benefits of foundational new technologies we’re making significant investments in.”
Work on CHERI (capability-system extension to RISC instruction set architectures) was initiated in 2010 by the University of Cambridge and SRI International and supported by DARPA, and was first demonstrated in 2014 as a prototype FPGA-based soft processor core named BERI, based on a 64-bit MIPS processor. Since then, the University of Cambridge led research has been working actively to bring CHERI to the ARMv8-A and RISC-V ecosystems, both supported by DARPA.
The collaboration with Arm started in 2014, to develop an experimental integration of CHERI with 64-bit ARMv8-A. It is creating an experimental superscalar CHERI-ARM processor (based on the Neoverse N1), SoC, and evaluation board (Morello) to be available for academic and industrial research from late 2021. Since 2017 the researchers have also been creating an experimental adaptation of CHERI to the 32-bit and 64-bit RISC-V ISAs, including multiple FPGA prototypes based on Bluespec and MIT BSV-language cores. CHERI ISAv7 includes a fully elaborated version of the CHERI-RISC-V ISA.
CHERI: overcoming market failure in security
So, the question is, why CHERI? Well, the premise is that mainstream computer systems are chronically insecure. Conventional hardware instruction sets and the C/C++ programming languages, dating back to the 1970s, provide only coarse-grained memory protection. This turns many coding errors into exploitable security vulnerabilities.
The development of the Morello board by the Arm consortium is part of a broader UK government program under its Industrial Strategy Challenge Fund (ISCF), to fund research and innovation in various strategic areas. Security is one of these, for which it launched its Digital Security by Design (DSbD) initiative in September 2019, a $244 million (£190 million) research program to explore potential applications of CHERI.
As part of this, UKRI (UK Research and Innovation) and Arm announced that the Arm Morello board will become available from 2021: a prototype 7nm high-end multi-core superscalar ARMv8-A processor (based on Arm’s Neoverse N1), SoC (system on chip), and board implementing experimental CHERI extensions.
In addition, as part of this effort, the UK Engineering and Physical Sciences Research Council (EPSRC) also announced a new $10 million (£8 million) program to fund UK academics to work with Morello. Arm will release its Morello adaptation of the University of Cambridge’s CHERI Clang/LLVM toolchain, and the university will release a full adaptation of its open-source CHERI reference software stack to Morello (including the CheriBSD operating system and application suite) as foundations for research and prototyping on Morello.
The vision for the DSbD initiative is to “overcome the market failures and radically update the foundation of the insecure digital computing infrastructure that underpins the entire economy.” John Goodacre, a key proponent of this program at Arm before he left the company last year, and now the challenge director for the DSbD program, told EE Times of the wider impact. “Though this is RISC-based, the fundamental technology should be available to apply to any processor technology.”
He said the funding programs are about opening up opportunities beyond just the technology — it addresses everyone from those building the chips to the users and those impacted. For this, he said there are three aspects to the program – enable, use, and impact.
On the enable front, this means developing the technology platform prototype, delivering a proven secure-by-default hardware evaluation board and system software. The ‘use’ involves community engagement and collaborative R&D to understand and enable market use, including tooling and processes to utilize the new capabilities. On ‘impact’, this will involve business-led demonstrators for sector-specific adoption, such as for IoT, connected vehicles, or financial services, to showcase real-world impact and move beyond the accepted norm.
The Arm Morello prototype
In a blog post, Arm’s Richard Grisenthwaite said the Morello board will enable industry partners to assess the security benefits of a range of prototype architectural features in real-world scenarios. “Creating the Morello prototype board commits Arm to more than £50 million worth of engineering and research. The ultimate goal is to design a new Arm-based platform that will make it far harder for bad actors to take full control of a compute system — even if they manage to hack it,” he comments.
The hardware capability technology used in CHERI, and in the Arm prototype architecture, combine the following: references to memory locations (i.e. pointers) with limits as to how the references can be used; the address ranges that they can use to access; and which functionality they can use to access.
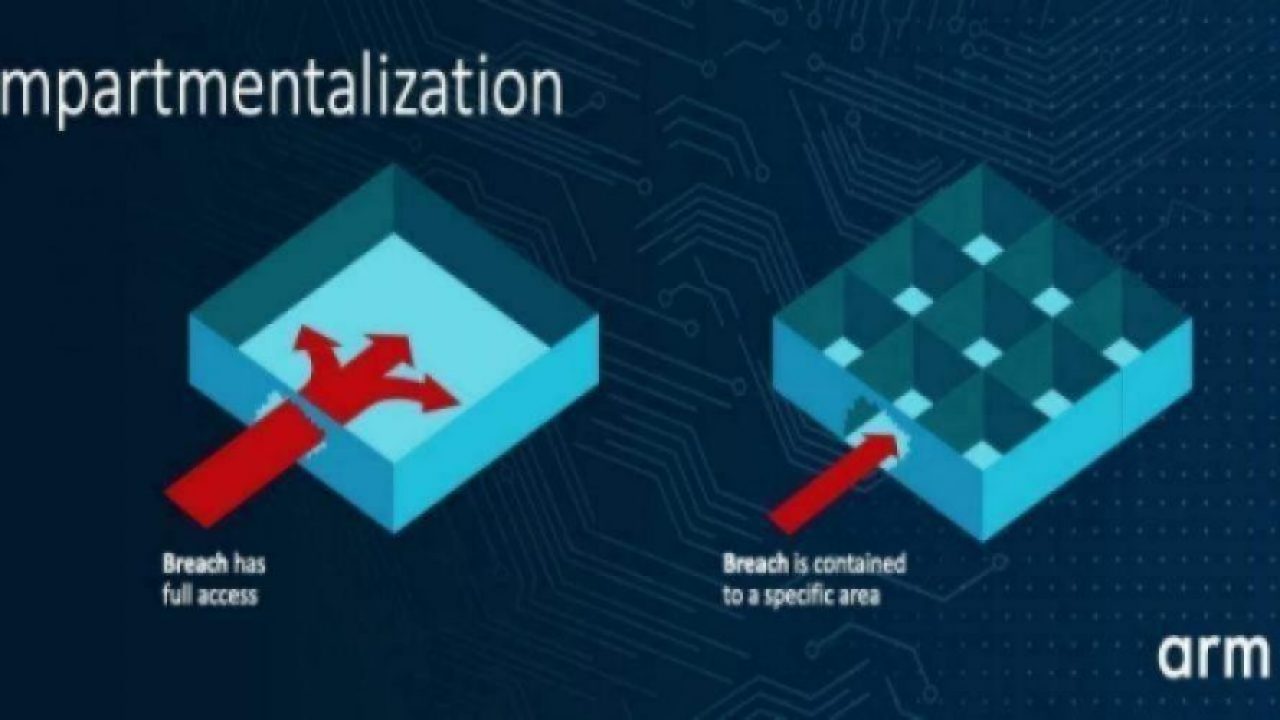
This combined information, known as a “capability”, is constructed so it cannot be forged by software. By replacing pointers with capabilities in a program, the memory safety is significantly improved, a critical step for stronger security. Beyond memory safety, it is also possible to use the capabilities of a building block for more fine-grained compartmentalization, creating software inherently more robust against attacks. In simple language, compartmentalization isolates different parts of critical code in individual ‘walled’ areas, with no access to any other area. The idea is that even if an attacker reaches one piece of the code or data, they will be unable to access any other piece, effectively being ‘trapped’ in one small zone.
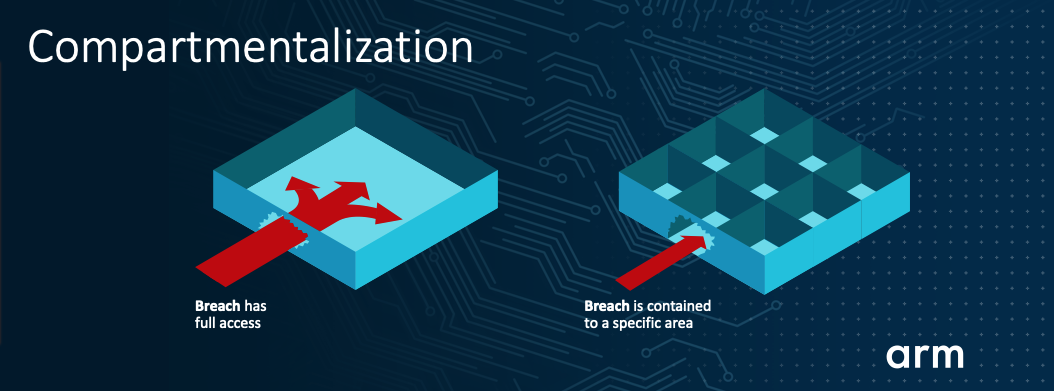
Compartmentalization isolates different parts of critical code, so even if an attacker
reaches one piece of code or data, they will be unable to access any other piece (Source: Arm)
Putting this in the context of today’s compute hardware, current architectural approaches do not allow for fine-grained compartments to be constructed in a performance-efficient way. So, in addition to hardware changes, the proposed new security approaches will also need software code to be written and compiled in radical new ways.
Grisenthwaite said for programmers to support this transformation, a commercial-grade hardware platform like the Morello board is vital so they can experiment and prototype for today’s highly complex software workloads. He added this is why the commitment from Microsoft and Google to the DSbD project is essential as their programming teams can create new software capable of taking full advantage of the new architectural features being developed.
What exactly is CHERI and the ‘capability system’?
CHERI is an ongoing research project that revises the hardware/software architectural interface with hardware support for capabilities that can be used for fine-grained memory protection and scalable software compartmentalization. It is based on the capability system, a design pattern for how CPUs, languages and operating systems can control access to resources. Capabilities are communicable, unforgeable tokens of authority, so capability systems are those in which resources are reachable only via capabilities. Such systems limit the scope and spread of damage from accidental or intentional software misbehaviour.
Capability systems make it natural and efficient to implement two security design principles in software. The first is the principle of least privilege, which dictates that software should run with the minimum privileges to perform its tasks; the second is the principle of intentional use, which dictates that when software holds multiple privileges, it must explicitly select which to exercise.
Based on this, CHERI is an architectural protection model, which composes the capability system model with hardware and software and adds new security primitives to instruction set architectures (ISAs) to enable fine-grained memory protection and highly scalable software compartmentalization. It is implemented by microarchitectural extensions to the CPU/SoC. Hence it enables new security behavior in software and mitigates vulnerabilities in C/C++ trusted computing bases.
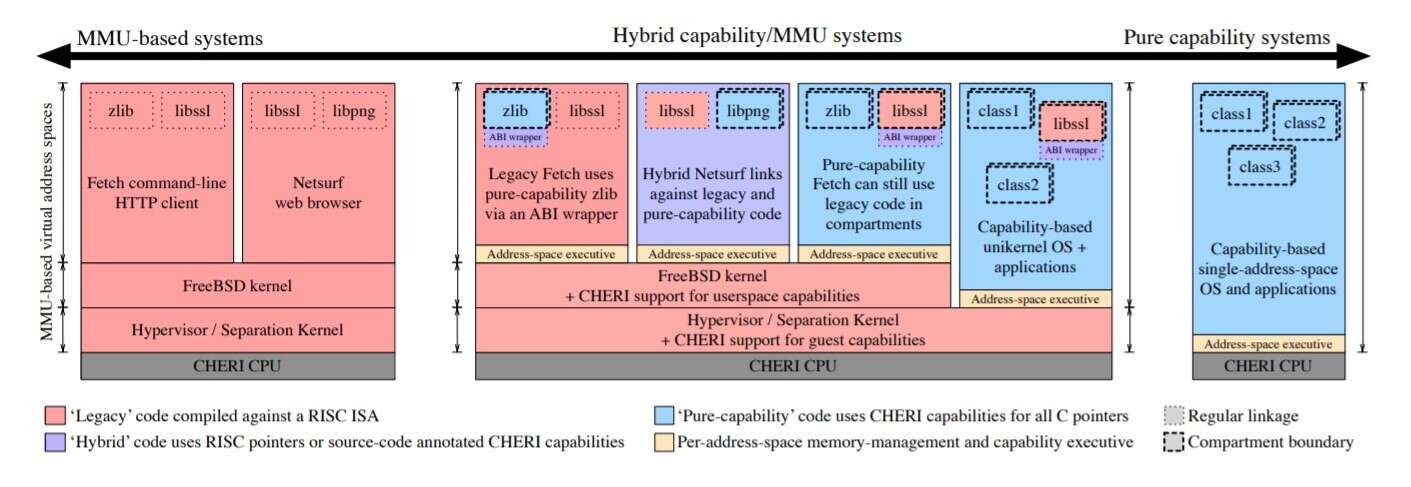
CHERI supports a wide range of operational software models including: unmodified MMU-based RISC operating systems; hybrid operating systems utilizing the MMU to support a process model and/or virtualization while using CHERI within virtual address spaces; and pure single-address-space CHERI-based operating systems.
(Source: University of Cambridge Computer Laboratory Technical Report, “Capability Hardware Enhanced RISC Instructions: CHERI Instruction-Set Architecture (Version 7)”, June 2019)
The work on CHERI was first presented at the 2014 International Symposium on Computer Architecture (ISCA) in Minneapolis. This was first prototyped via an FPGA-based soft processor core named BERI, based on a 64-bit MIPS processor. It is a hardware/software/semantics co-design project, combining hardware implementation, adaption of mainstream software stacks, and formal semantics and proof. The CHERI ideas have been developed first as a modification to 64-bit MIPS and now also for 32/64-bit RISC-V and 64-bit ARMv8-A. A complete software stack for CHERI has been prototypes by adapting widely used open-source software such as Clang/LLVM, FreeBSD, FreeRTOS, and applications such as WebKit, OpenSSH, and PostgreSQL. The architecture has been formally modeled and a number of proofs about its security constructed, with the models also used for microarchitectural validation in the prototypes. These models also have the potential to support further activities such as formal proofs about software and microarchitecture.