Microsoft and Google Planning Silicon-Level Security
Article By : Rick Merritt

Low-level solutions to problems like Spectre and Meltdown being sought
CUPERTINO, Calif. — Experts called for a new generation of secure-by-design computers at the Hot Chips conference here. In small steps in that direction, Microsoft and Google described their separate but similar hardware security architectures.
The Spectre/Meltdown vulnerabilities disclosed in January woke engineers up to how decades-old techniques such as speculative execution also could be doors to side-channel attacks. Red Hat alone spent tens of thousands of engineering hours patching those flaws in Linux, a fraction of the work also in progress at chip makers such as AMD, Arm, IBM and Intel estimated to cost the industry millions of dollars.
Today’s patches manage but don’t fix underlying vulnerabilities, some of which may persist for years, experts said. New variants of the attacks emerged as recently as last week and are expected to keep cropping up for the foreseeable future.
“There are a lot of side channels, and closing them all is impossible… This is a whole set of things to change, and it will take a long time,” said John Hennessy, chairman of Google parent Alphabet and a veteran processor architect, in a keynote calling for the start of a new security era.
Red Hat worked on an initial set of Spectre/Meltdown patches for eight chip architectures across 15 versions of Linux, representing 10,000 hours of engineering. New variants discovered last week “already costed us more than 10,000 hours” in part because they involved both the kernel and the hypervisor, said Jon Masters, who oversees the work at Red Hat.
“We need computer architecture 2.0 that defines computing that doesn’t leak — the only problem is we don’t know how to do it,” said Mark Hill, professor of computer science at the University of Wisconsin at Madison, in a panel discussion here.
Hill suggested a laundry list of techniques for securing processors such as isolating branch predictors, partitioning caches and reduce aliasing. “There are many possibilities, and none of them feel good to me yet,” he said, noting it’s not clear whether the security problem can be fixed or simply managed.
“I’m delighted to hear people like John Hennessy call this an era of security — it’s better late than never,” said Ruby Lee, a veteran security researcher from Princeton who attended the event.
“It’s good were not just looking at fixes one problem at a time — that’s what the security industry has tended to do…[The first principle for a secure architecture should be] no access without authorization,” she added.
Several speakers called for work in open-source software and hardware. “We have seen a lot of attacks against microcode of closed, undocumented behavior in machines — it’s hard to trust what you can’t see,” said Masters.
Google and Microsoft pursue parallel paths
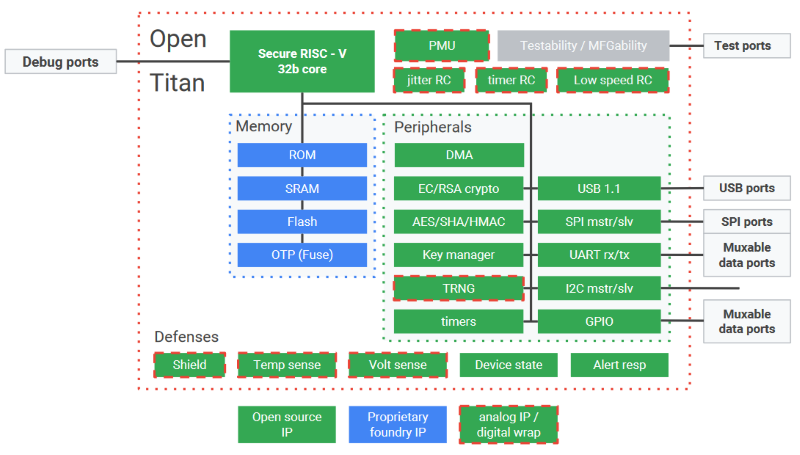
In separate talks, Microsoft described the Pluton security block for its Azure IoT service and Google detailed Titan, a similar block used to tag and secure systems in its data centers. Despite their very different targets, the two approaches had remarkably similar principles and features, leading one Google engineer to suggest they might someday converge into one standard.
Both Pluton and Titan enforce use of encrypted certificates for secure system boots and device identification. Both chips include random number generators and all the hardware blocks needed to generate keys not available to software. In addition, they both use e-fuse settings to control the state of the blocks to prevent tampering through their manufacturing and life cycle.
One of the biggest differences in the two approaches is how they will come to market. Microsoft worked with Mediatek on the first implementation of Pluton inside a Wi-Fi router chip. It aims to work with other MCU and SoC vendors yet to be announced.
So far, Google created two implementations of Titan. One was announced last year for securing its data centers and described in detail here. Another less well-known version is in use by thousands of Google employees today as a second-factor authentication in USB dongles.
Google is forming an industry group to launch, probably next year, work on an open source implementation of Titan, possibly based on a 32-bit version of a RISC-V core. The open variant is geared for broad use in any embedded or consumer product.
Engineers for the search giant hope the so-called Open Titan effort could attract others such as Microsoft. A merged effort could form a de facto standard that over time could hammer out something like the secure architecture Hill and others described. However, for today that concept is just a gleam in the eyes of some Google engineers.
In the short term, Microsoft hopes Pluton becomes a selling point for its Azure IoT cloud services. A wide variety of companies including other cloud service providers and MCU vendors are expected to roll out their own security architectures and implementations.
The good news is in the wake of Spectre/Meltdown, engineers are motivated to build much more secure products. The bad news is they fear it may take other more painful hacks before their customers are willing to pay for them.
— Rick Merritt, Silicon Valley Bureau Chief, EE Times 
Subscribe to Newsletter
Test Qr code text s ss